School Security Solutions
Preventing and Reducing School Threats
Understanding the evolving nature of school threats is essential for prevention and mitigation efforts. There has been a recent increase in threats from state-sponsored terror groups targeting schools, and it highlights the need for a comprehensive approach to address this issue.
The two groups that make up most school threats are students and terrorists/criminals. Historically the majority of school threats were more likely to come from within the student population. In the last five years that has changed. In fact, in the last two years, a high percentage of the threats have come from state-sponsored terror groups. Terror groups are also behind some of the TikTok challenges that encourage students to commit threats. Terror groups account for a very high percentage of the lost instructional hours.
Terror groups historically used email to send out threats, they have moved to Bot farms that use social media, auto-dialers, and free phone calling apps to deliver threats. They still try and use email, but most schools have email filters that already prevent email threats from being delivered.
Copycats: When overseas groups commit threats and no one is caught, it gives students the false impression they can get away with making a threat and it increases the number of threats made by students.
Technology, education, behavioral health, and law enforcement can impact a student's willingness to commit a school threat, however, you cannot impact a terror group's willingness to commit a threat. The only way to stop threats from terror groups is to use technology that prevents them from gaining access to schools.
Pricing:
The cost is $1.50 per student per year plus a one-time installation fee. Support hours can be purchased if required.

School Access Manager
School Access Manager (SAM) is a suite of products. It prevents/reduces swatting, shooting threats, bomb threats, Apple AirDrop threats, social media threats, notes left in school, verbal threats, email threats, bullying, and harassment using advanced technology and innovation to ensure your school's safety and security.

SAM currently uses three approaches to prevent and reduce school threats.
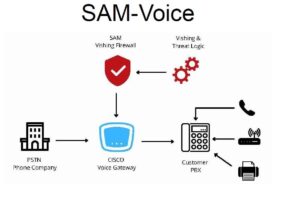
SAM Voice looks at all incoming calls to determine who should be allowed into the school. Think of it like an electronic SRO.
Sam Voice is very effective against swatting and threats that are called into a school. These types of threats are impossible to stop without SAM Voice and they are the threats that cause the largest loss of instructional hours.
Currently, AirDrop messages can’t be tracked. Even Apple cannot look at a message and determine who sent the message. AirDrop does not have an audit log, and the user information is encrypted.
This has created the ability to send anonymous messages in AirDrop. Some students have taken advantage of the messages being anonymous and sent threats using AirDrop. More recently, schools have had evacuations and lockdowns as a result of these anonymous AirDrop threats. This has led to lost instructional time, which impacts a student’s progress, increases emotional stress, and costs taxpayers money. Airlines are starting to experience the same AirDrop threat issues.
Solution
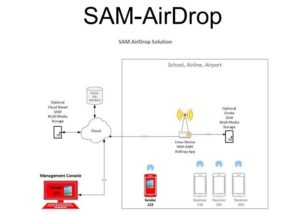
Installed network devices that capture airdrop information. Create an audit log and decrypt limited user information to identify the sender. The network devices must be installed before a message is sent to capture the message and create an audit log.
Simple User Interface
Photos are presented like a photo contact sheet; next to each photo, expose the phone number of the device that sent the photo.
We capture the email of the device that sent the message but do not decrypt the email. If validation in addition to the phone number of the device is required, allow an administrator to enter the email address associated with the device. The system will compare the email entered with the captured email and indicate if it matches.
Network Devices
Airdrop uses both Bluetooth and peer-to-peer Wi-Fi to communicate between devices.
The application runs on a standard Linux device, making the hardware affordable.
This also allows the users to use off-the-shelf features like POE (power over ethernet) and other standard hardware features. This makes the complete solution affordable.
Other Use Cases
In addition to preventing school threats, there are other use cases:
-
- AirDrop Threats
- Securing Test Environments
- Electronic Harassment
- Electronic Bulling
SAM AirDrop monitors Apple AirDrop networks operating within the school. It creates an audit log of messages sent within the school including who the sender was. If a student sends a threat message it is easy to determine who the student was. This can also be used in cases where a student uses airdrop for harassment or bullying.
- Airline AirDrop Security
- Theft of data
- AirDrop and its logos are trademarks of Apple Inc.
 School Posters - We came up with a different, proactive prevention approach. We studied thousands of school threats and determined that most were viewed as harmless pranks. Even though we had a solution to prevent swatting, most adults and students still viewed most school threats as pranks. Our approach was to develop a database that could put a value on the threat. We felt if we could show the cost of a threat, it would start to change the perception from a prank to something more serious. We met with just under 50 school business officials and explained our methodology. By the time we were done, we had a formula that was acceptable. It took a great deal of work because every state has different requirements for the number of days and the number of hours. It took us over a year to collect all of that. Then we had to collect all the school budgets to apply our formula. That is a huge ongoing task.
School Posters - We came up with a different, proactive prevention approach. We studied thousands of school threats and determined that most were viewed as harmless pranks. Even though we had a solution to prevent swatting, most adults and students still viewed most school threats as pranks. Our approach was to develop a database that could put a value on the threat. We felt if we could show the cost of a threat, it would start to change the perception from a prank to something more serious. We met with just under 50 school business officials and explained our methodology. By the time we were done, we had a formula that was acceptable. It took a great deal of work because every state has different requirements for the number of days and the number of hours. It took us over a year to collect all of that. Then we had to collect all the school budgets to apply our formula. That is a huge ongoing task.
When you combine our technology, the risk of consequences, and student education it is a very effective deterrent.
Posters
We provide the data to allow school posters to articulate the consequences of a threat:
- Criminal – List the penalties for making a school threat.
- Financial – List the amount of money a person can be held liable if they make a school threat.
We maintain a threat database for every school in the United States. The database maintains the instructional hour requirements of each state and the school budgets. We use this data to calculate the cost of an instructional hour.
Student Educational Videos
We create student educational videos that explain the various threats and how law enforcement and Congress have new tools that allow them to trace who sent the threat. Most videos will be less than 5 minutes and can be customized to each district upon request.
List of current and upcoming educational videos:
- Making Fake Threat calls and Swatting
- Social Media and TikTok threats
- Leaving threatening notes in school
- Email threats
- Verbal threats
Introduction Video
A Solution to School Threats
https://tdrtechnologysolutions.com/wp-content/uploads/2023/10/SAM-School-Threat-Prevention.mp4
SAM Voice has been updated to protect 911 centers from swatting and other school threats that are called into 911 centers.
